One year ago we found that using the Word 2003 XML format could by very usefull for pentesters/redteamers/attackers as a standard VBA meterpreter payload was scoring 1/57 on VT (instead of 20/57 using the Office OpenXML format). AV vendors made their homeworks, VT score is now 14/54
Anyway another very simple trick can help a lot: by embedding the exact same file (xmhell.xml) in a new word document and saving it as a Word 2003 XML again you’ve got a 0/54 on VT ! Oh yeah !
Update (2016-03-31):
2 months after submitting our payload on VT, the file still scores 0/56…
It seems that AV don’t like russians dolls, even Kaspersky and yet it contains a straight meterpreter payload (without encoding) which is normally catched.
Ok, but pwning a victim by this trick is not so obvious:
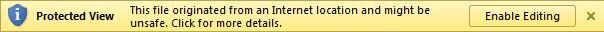
- the victim has to open the babushka.xml file:
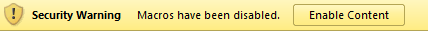
 2. then open the xmlhell.xml file that is embedded and then accept a first warning:
2. then open the xmlhell.xml file that is embedded and then accept a first warning:
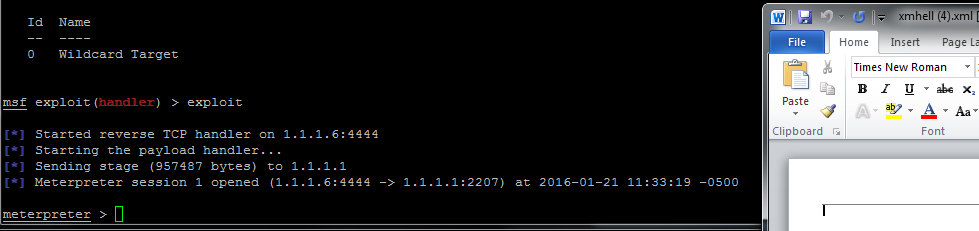
And then:
But users are… users ! They will click and click again.
What about sandbox analysis ?
The excellent Payload Security VxStream sandbox [flags] (https://www.hybrid-analysis.com/sample/84ccff8e97cbb57c74615748d9c340d8cfe2363bf9b432b251013d5ad7f6909d?environmentId=1) our original xmhell file:
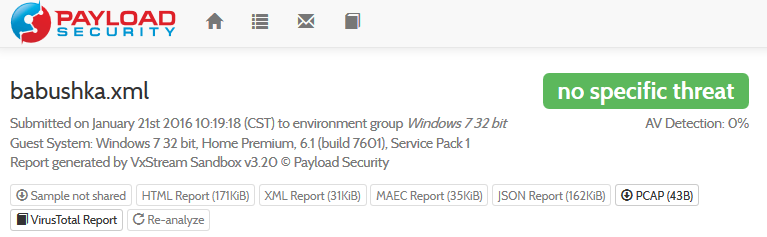
But not the babushka variant:
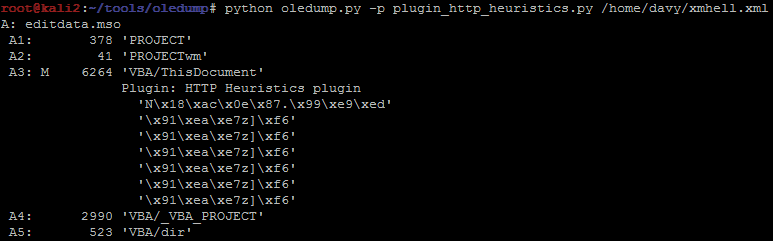
What about a quick and dirty static analysis with olevba and oledump ?
Oledump catches VBA in xmhell.xml but we already knew that:
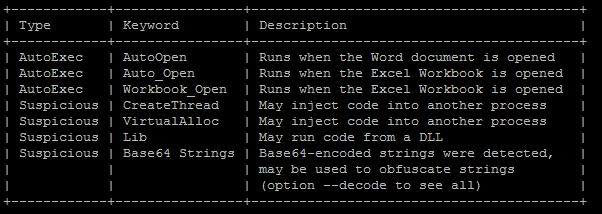
Olevba works very well too:
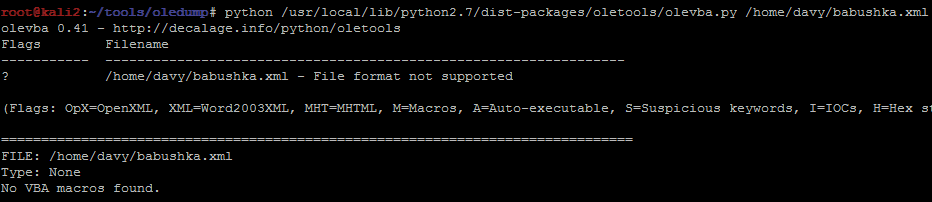
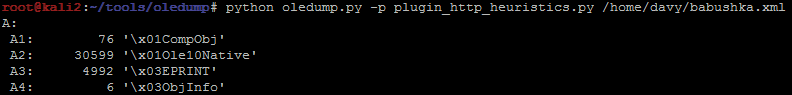
But that’s not the same story for babushka.xml:
That’s all for now, happy hunting and happy pwning !