Davy Douhine
Pentest
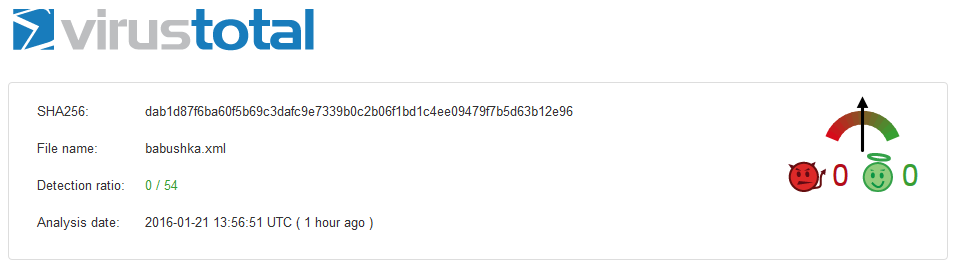
Update (2015-07-07) 6 months after submitting our first Word 2003 XML payload on VT, the file now scores 9/53… Still not enough.
If you are a pentester and your target doesn’t run one of these 9 AV, you’re in !
Update (2015-04-27) 3 months after submitting our first Word 2003 XML payload on VT, the file now scores 9/56.
Which means Symantec, McAfee, Sophos and a few others considered this threat seriously.